Web Application Firewall Solutions
A WAF creates a shield between a web app and the Internet; this shield can help mitigate many common attacks.
Introduction
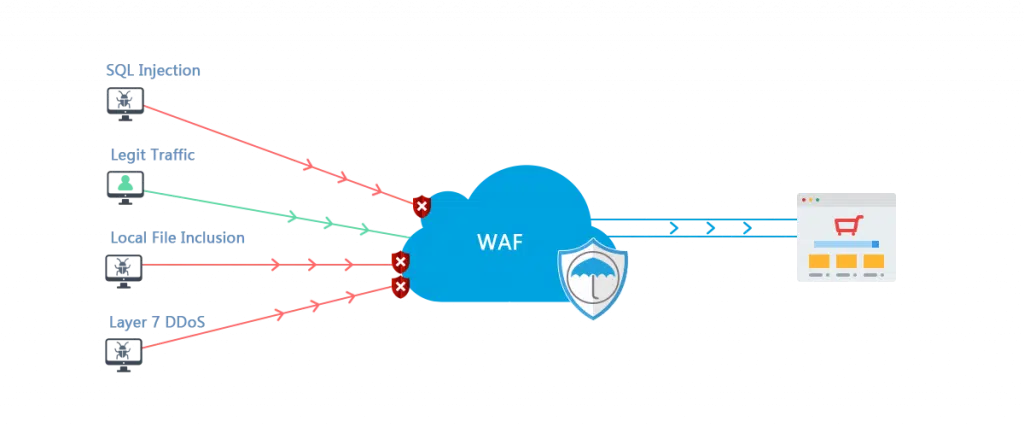
A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It typically protects web applications from attacks such as cross-site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection, among others. A WAF is a protocol layer 7 defense (in the OSI model), and is not designed to defend against all types of attacks. This method of attack mitigation is usually part of a suite of tools which together create a holistic defense against a range of attack vectors.
By deploying a WAF in front of a web application, a shield is placed between the web application and the Internet. While a proxy server protects a client machine’s identity by using an intermediary, a WAF is a type of reverse-proxy, protecting the server from exposure by having clients pass through the WAF before reaching the server.
A WAF operates through a set of rules often called policies. These policies aim to protect against vulnerabilities in the application by filtering out malicious traffic. The value of a WAF comes in part from the speed and ease with which policy modification can be implemented, allowing for faster response to varying attack vectors; during a DDoS attack, rate limiting can be quickly implemented by modifying WAF policies.
Types of WAF Solutions That Are Available
A WAF can be implemented one of three different ways, each with its own benefits and shortcomings:
- A network-based WAF is generally hardware-based. Since they are installed locally they minimise latency, but network-based WAFs are the most expensive option and also require the storage and maintenance of physical equipment.
- A host-based WAF may be fully integrated into an application’s software. This solution is less expensive than a network-based WAF and offers more customisation. The downside of a host-based WAF is the consumption of local server resources, implementation complexity, and maintenance costs. These components typically require engineering time, and may be costly.
- Cloud-based WAFs offer an affordable option that is very easy to implement; they usually offer a turnkey installation that is as simple as a change in DNS to redirect traffic. Cloud-based WAFs also have a minimal upfront cost, as users pay monthly or annually for security as a service. Cloud-based WAFs can also offer a solution that is consistently updated to protect against the newest threats without any additional work or cost on the user’s end. The drawback of a cloud-based WAF is that users hand over the responsibility to a third party, therefore some features of the WAF may be a black box to them.
Why choose SR Cloud Solutions?
SR Cloud Solutions has a 25-year track record of supplying managed security services to many organisations in different industries.
- The best technology – highest levels of accreditation with the world’s leading vendors such as Imperva, Cisco, Fortinet, and Palo Alto.
- Skills and expertise with a UK-based 24/7 Security Operations Centre (SOC).
- We are a Joscar accredited business which means we are certified to work with leading defense companies who require the highest standards of cyber security.
- We are experts in Cloud infrastructures such as Microsoft Azure so we can provide expert security consultancy on hybrid cloud environments and how best to secure and monitor those environments including Cloud Governance.
Book a meeting with one of our consultants to learn more or read on more below to find out more about our Web Application Firewall Solutions.
Web Application Firewall Benefits

Prevents Cookie Poisoning
Cookie poisoning, also known as session hijacking, is when a cybercriminal manipulates or forges a cookie to bypass security or gain access to the server to steal data. This type of attack is used when a user is required to login to an account and the cybercriminal intercepts the cookie to extract saved information from it, such as auto-filled personal information. WAFs can prevent this from happening by protecting and encrypting personal identifiable information as well as identifying altered or "poisoned" cookies from reaching the server.

Prevents Cross-Site Scripting (XSS)
Similar to cookie poisoning, Cross-Site Scripting, or XSS, is a type of injection involving malicious scripts. Cybercriminals send malicious code through the web application directly to a different end user to attempt to access cookies or other sensitive data saved in the browser and used by the web application. WAF can help prevent against this with configured policies to scan and monitor these requests and block them when safe conditions are not matched. If identified by the WAF as malicious XSS code, it will block it from gaining access.

Prevents SQL Injection
SQL stands for Structured Query Language and is a common programming language. SQL injection is when a cybercriminal modify queries an application makes which can grant them access to important personal or financial information. WAF can prevent against this by running off rules that require SQL injections to match specified conditions and if they do not, it will block the user from even reaching the web application.

Blocks Distributed Denial of Service (DDoS)
This type of attack involves several devices that have been infected with malware overwhelming a web application by creating an unusual amount of traffic. This causes a denial-of-service to normal traffic, cause performance issues, and weaken the layers of security. A WAF can identify and block this type of unusual activity based on key indicators such as high levels of traffic from a single IP address, unusual traffic matters, or high traffic on a specific page.
Join Other Leading Companies Who Trust SR Cloud Solutions







Frequently Asked Questions
Web Application Firewalls, or WAF, block an ever-expanding list of sophisticated web-based intrusions and attacks that target the applications hosted on web servers and the sensitive or confidential data to which they have access.
Does your organisation have a website or other web applications? If you answered yes, then you should consider using a WAF. Even small websites are a target for cybercriminals, especially since this type of security is often neglected in small organisations, putting you at risk regardless of how unlikely you perceive it to be.
Nearly 70% of all websites use HTTPS, an important first step in securing any data your website collects, such as customer or payment information. Unfortunately, HTTPS is the bare minimum security requirement, and is not enough to stop cybercriminals from infiltrating your database and stealing sensitive customer information. Because a WAF uses a set of policies to filter and block unwanted web traffic as well as protect against the most common types of hacks on a continuous basis, it can help secure you in ways the HTTPS is unable to. It also helps increase site speed and performance by using caching mechanisms.
While it is wise for any organization with a web application to have a WAF, some specific types of organizations who may be more prone to web attacks include:
-E-commerce sites
-Online financial services
-Lead generation sites
-Online healthcare services
-Any organisation required to follow compliancy standards such as PCI DSS or HIPAA.
Just as your organisation’s firewall stand as a shield around your IT infrastructure to filter traffic and protect against cybercriminals, your WAF is a firewall that shields your web applications from the same kind of malicious activity. A WAF protects by monitoring the HTTP traffic and filtering out malicious activity to prevent it from reaching the server. WAFs run off a set of policies to help determine what traffic is malicious by indicating what vulnerabilities and traffic behavior to identify.
WAFs can be configured into three general models: Whitelisting, Blacklisting, and Hybrid. Whitelisting tells the WAF to only allow in traffic that has been pre-approved and meets specified criteria. Blacklisting is configured to block known vulnerabilities and malicious signatures but allow all other traffic. Hybrid is configured to incorporate both whitelisting and blacklisting methods for the specific need of the web application.
There are three types of WAFs available on the market. They all accomplish the same goal but are installed and deployed in different locations. Because of this, the three types differ in cost, maintenance required, and speed.
Hardware-based WAF
A hardware based WAF is one that is installed locally within the LAN, or local area network, and deployed on a physical piece of hardware. The operating system runs within the appliance and supports any updates for the WAF.
Software-based WAF
A software based WAF is installed in a Virtual Machine, or VM, rather than hardware. This option functions the same as the hardware based WAF, but allows for increased flexibility as it can be used on-premise or in the cloud such as Azure or AWS and has a decreased cost because there is no hardware required.
Cloud based WAF
A cloud based WAF is offered as a SaaS, or software as a service, structure. With this option, the WAF is located entirely in the cloud and everything is managed by the service provider. This creates the most simple way for organisation’s to deploy and maintain a WAF, as the service provider will optimise and update as needed. This option may be best for organizations that have limited IT resources to maintain and manage their WAF.
Speak to one of our security EXPERTS
Our team is available for a quick call or video meeting. Let's connect and discuss your security challenges, dive into vendor comparison reports, or talk about your upcoming IT-projects. We are here to help.


